[Courtesy of LG Uplus]
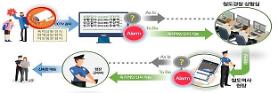
Intelligent CCTVs analyze various images to distinguish physical appearances or detect emergencies. However, video images containing sensitive personal information can be leaked through hacking.
In cooperation with ICTK Holdings, a security company specializing in internet of things (IoT), LG Uplus (LGU+) has developed a solution using a physically unclonable function (PUF) that was applied to a virtual private network (VPN) between CCTVs and servers to prevent hacking and safely deliver videos through security authentication in several stages.
PUFs provide a physically defined "digital fingerprint" output that serves as a unique identifier. Often based on unique physical variations which occur naturally during semiconductor manufacturing, PUFs are implemented in integrated circuits and are typically used in applications with high-security requirements.
LGU+ would complete the demonstration of its new technology by October 2022. Afterwards, a PUF VPN infrastructure that can handle 100,000 CCTV cameras will be set up for commercialization at an internet data center in western Seoul.
"PUF VPN will be applied not only to CCTVs but also to other services, and we will continue to make efforts to secure VPN security technology with quantum-resistant cryptography within the year so that customers can trust and use the service," LGU+'s corporate service development lab head Jeon Young-seo said in a statement on June 23.
In April 2022, LGU+ launched South Korea's first commercial service of quantum-resistant cryptography that provides an optimal network for customers who require security services that can safely protect data from external threats.
As different passwords are used for all IT-related hardware and software with many companies storing and processing numerous big data, a system to prevent the risk of hacking is important. Data encoded in a quantum state is virtually unhackable without quantum keys which are basically random number tables used to decipher encrypted information. Even though current, publicly known, experimental quantum computers lack the processing power to break any real cryptographic algorithm, cryptographers are designing new algorithms to prepare for a time when quantum computing becomes a threat.
Copyright ⓒ Aju Press All rights reserved.